FR-MOTP
Facial Recognition – Mobile One Time Password
FR-MOTP
Multi-factor Authentication System with Facial Recognition
FR-MOTP is a verification system that authenticates people in enterprises and organizations with facial recognition, a mobile app, one-time passwords, and a server. With its multi-layered approach to protecting users from identity theft and brute force attacks, this innovative security solution enhances your safety even if one layer fails.
FR-MOTP
Benefits
Enhanced Security with Multi-layered Approach
User-friendly Facial Recognition Mobile App
Seamless Authentication and Enrollment Process
Guard Against Phishing with OTPs and Facial Recognition
Versatile Deployment with Integration Across Existing Systems
Easily Manage and Track Compliance with Any Industry Regulations
FR-MOTP
Key Features
Facial Recognition Authentication
Perform real-time facial recognition with edge AI biometric technology to prevent unauthorized access.
Mobile App Authentication
Perform facial recognition and access to a one-time password on a mobile app.
Server-Side Authentication
Validate and record authentication attempts with a centralized control and auditing server.
FR-MOTP Server Storage
Easily store biometric data, login attempts, intrusions, and employee attendance on a secured server either on-site or on the cloud.
Scalability and Deployment
Easily integrate and deploy with existing systems across multiple locations.
FR-MOTP
How it Works
01
Enter your PIN Code on the Mobile App
02
Perform Facial Recognition Using the App
03
Receive a One-time Password and Log In
Verification records are securely stored on the FR-MOTP server for auditing purposes.
FR-MOTP
Architecture
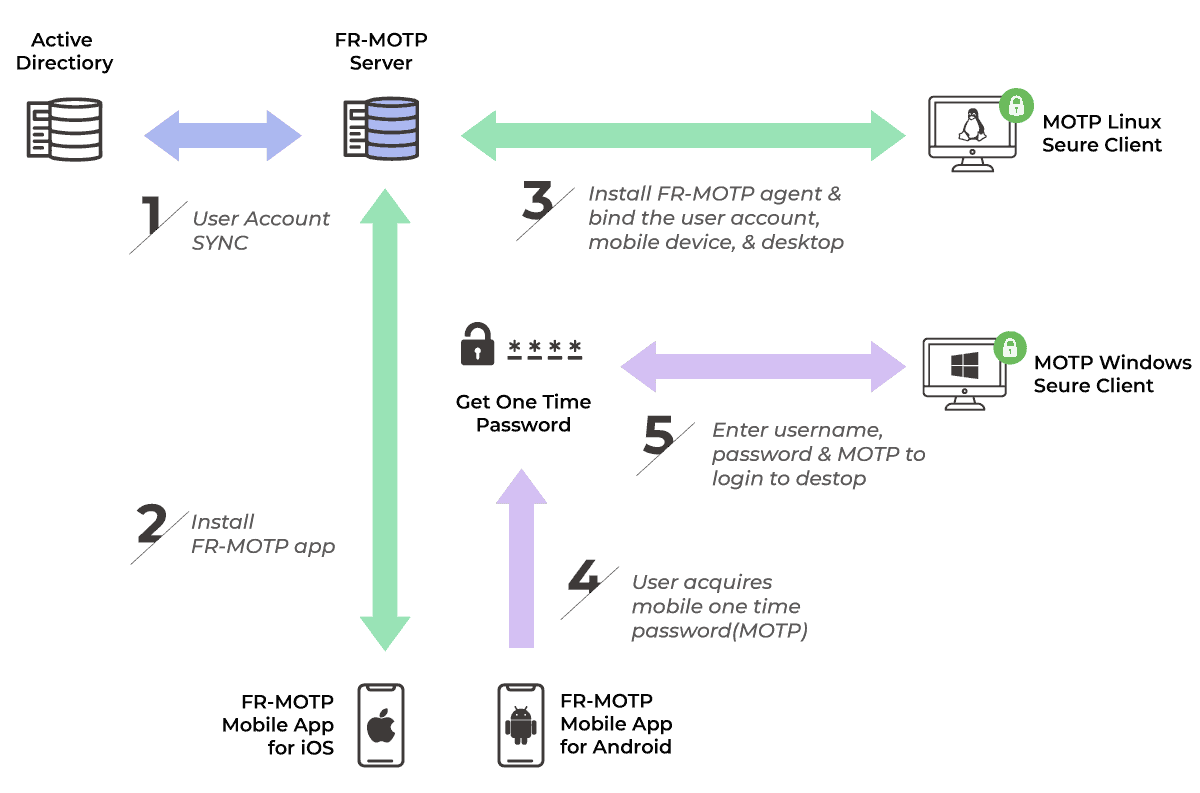

Discover why so many government agencies and enterprises chose FR-MOTP to authenticate their employees and further protect their operations.
Are You Ready to Unlock Enhanced Authentication with FR-MOTP?
Speak to our team of experts now.